Sniffers
Sniffers
Sniffing as in common terms means to look or find for something, like sniffer dogs do in crime scene investigation, so in the Hacking world we do use some tools called sniffers. These tools are used to capture traffic flowing on a network and then store and analyze them. The stored captures can be used to later check for configuration and passwords etc.
Sniffers are computer programs that help capture traffic or data flowing in and out of a system. These tools are mainly used to capture traffic and these tools normally do not modify the packets flowing.
In earlier days when phones were more popularly used, Wiretapping was done, which is the process of monitoring phone conversations and also Internet conversations. Such techniques were very popularly used during world wars to listen to communication between other countries.
Active Wiretapping: Is the process of listening to the conversation, recording, monitoring the conversation but also inserting or injecting something in the communication.
Passive Wiretapping: is the process of only listening and monitoring the traffic or conversation and collecting information or knowledge of what is happening.
NOTE: WIRETAPPING IS ILLEGAL AND CONSIDERED A CRIME IN MOST COUNTIRES. ONE NEEDS LEGAL PERMISSIONTO TAP COMMUNICATIONS.
PACKET SNIFFING
– This is the process where traffic is monitored going and coming out of the system
– Packet sniffing can be done using hardware and software
– It is similar to a wiretap, but this is mainly done on computer networks
– Using packet sniffers, an attacker can gain access to information about accounts, passwords etc.
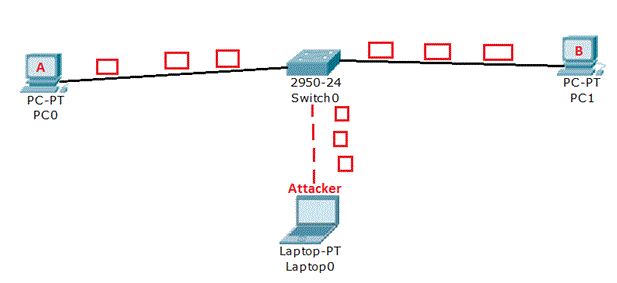
In the above image we see, that the device A is sending traffic / data to device B, but the attacked in between can start a sniffer and check or collect all data.
Sniffing Tools
– Wireshark / Ethereal: This is the most popular packet capture or sniffing tools. It is GUI based and offer many features to analyze the captured packet
– TCPdump: This is another commonly used traffic capture tool. You can get this at tcpdump.org. This mainly used in Linux.
– Windump: This is a part of the tcpdump but used for which shows header information etc.
– DSniff: This is used to sniff passwords and other protocols. This tool is also mainly used in Linux and UNIX environments.
There are many more tools, but Wireshark and tcpdump are the most popular among all of these.
Wireshark
This tool is available for both Windows and Linux and can be downloaded from https://www.wireshark.org/
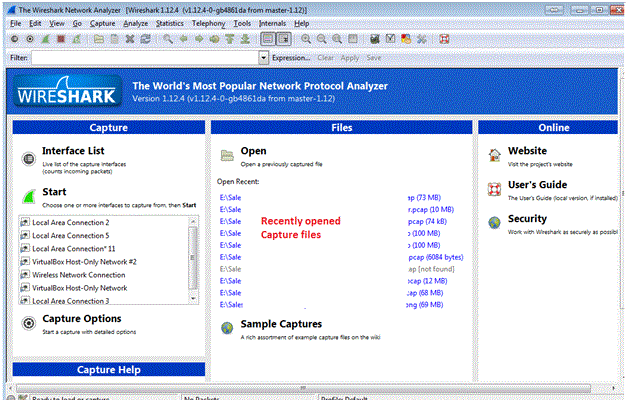
Once you open Wireshark you see the below screen
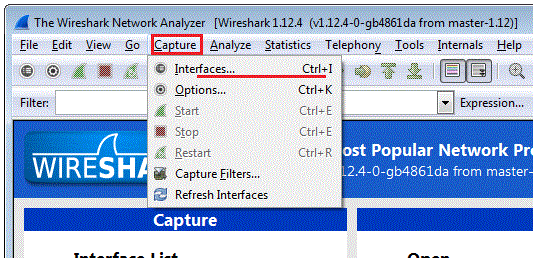
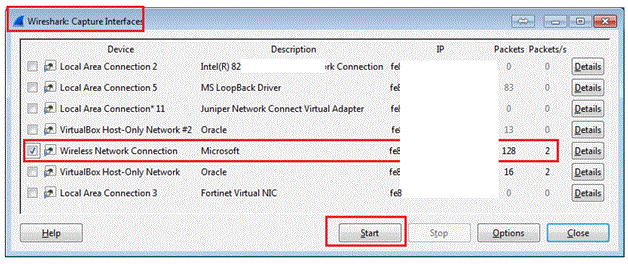
In the Captures, menu, you see option Interfaces
We see the list of Interfaces on the system. Select the interface on which you want to take captures. We also see some packets flowing on the Interface. In our case we selected the Wireless Network Connection
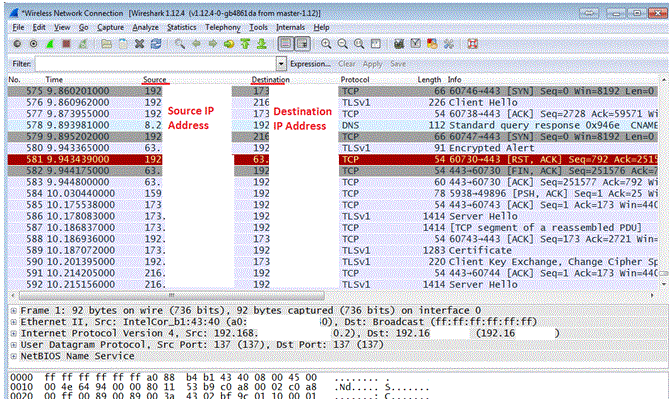
Once you click on “Start” you see packets in the Wireshark main window
Once you think you have collected sufficient information, you can click on Stop Button on the toolbar or Go to Capture Menu and Click Stop.
Then Save this capture and use it for analyzing.
There are some filters which are helpful in searching for information in the capture files.
| Operator | Function | Example |
| == | Equal | ip.addr == 192.168.1.2 |
| eq | Equal | tcp port eq 80 |
| != | Not Equal | ip.src != 192.168.1.2 |
| ne | Not Equal | ip.src ne 192.168.1.2 |
| contains | That contains specified value | http contains “http://www.abc.com” |
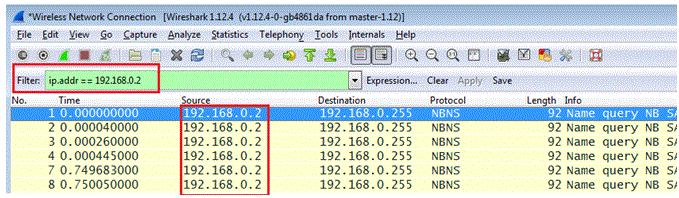
In the below screenshot we see that we have filtered only IP addresses 192.168.0.2, using the filter
“ ip.addr == 192.168.0.2”
Wireshark also comes with some inbuilt smaller CLI tools like below:
| Command |
Function |
| tshark | This is similar to Tcpdump, it’s the CLI of Wireshark |
| dumpcap | This is a smaller package that is intended to take captures only |
| mergecap | This is helpful in merging multiple capture files into one file |
| text2cap | Using ASCII hexdump, a capture is made |
| editcap | To edit or change or translate the format of the captured file |
| capinfos | After reading the capture provide info or statistics about it |
TCPDump
You can download TCPdump from the site http://www.tcpdump.org/
This tool is almost equally popular among Linux / UNIX users. This is a command line tool and is very good and reliable among some other available tools. This has been used even before Wireshark was used, thus it is a really well tested and used tool.
Sniffing Threats
The below are some types of information that can be stolen using packet sniffers
– Emails
– Web traffic
– ftp password ( as its clear text)
– chat session
– network device configuration, mainly router
– DNS traffic
– Telnet passwords ( as it is clear text)
– Traffic related to logs i.e. syslog
These days al devices are connected using Switches; there are certain types of attacks that can be done or possible in a switched environment.
- ARP Spoofing / Poisoning: ARP (Address Resolution Protocol) is the protocol that is used for IP to MAC address mapping. ARP Poisoning is the technique in which the ARP tables are messed up with and the mapping don’t point to the correct device. The attacker may spoof the ARP table and share its MAC address for some server IP and all client traffic will be sent to the hacker instead of the server.
- MAC Flooding: MAC is the hardware address of a device. The switches store this information with mappings to the IP addresses. An attacker can flood in many fake MAC address for some IP which the switch is unable to handle. The goal of the attacker is to get the switch in a state called “fail open mode”, in this mode the switch acts like a hub thus broadcasting all packets to all the ports. And the attacker can be sitting on one of those ports to sniff the packets
Countermeasures against Network sniffing
– Switches are configured with feature like Port Security, where only specific MAC addresses can send traffic through those switches
– Use of IPv6 is one way as it has security feature that IPv4 did not have
– Instead if using telnet, try to use ssh which is secure and encrypts the passwords sent
– Make use of Virtual Private Network (VPN) can be helpful as VPNs use encryption and do not allow someone to directly break in.
– Also making use of IDS, intrusion detection systems and NIDS, Network IDS can help fight sniffing attacks
Read more
- What is Ethical Hacking
- Footprinting and Reconnaissance
- Scanning Networks
- Trojans and Backdoors
- Enumeration Hacking Phase
- Social Engineering
Read more