Chapter 1 – Basic Network Security Concepts and Techniques
NETWORK SECURITY OBJECTIVES
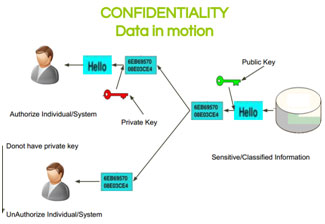
- Confidentiality
- Integrity
- Availability
ASSET
Asset = anything that is valuable to organization
Tangible Items
- People
- Computer
Intangible Items
- Intellectual Property
- Database Information
- Contact Lists
- Accounting Info
What is VULNERABILITY
Vulnerability = Exploitable weakness in system or design
Vulnerability can be found in
- Protocols
- Operating Systems
- Application
- System Design
What are LATENT THREAT, THREAT and THREAT VECTOR
- Threat = Any potential danger to asset
- Attacker launches attack, compromise security against an asset by exploiting existing vulnerability, this implies threat is realized
- Latent Threat = Vulnerability exist in system but not yet exploited
- Threat Vector =Agent that take advantage of vulnerability is called threat agent or threat vector
What are COUNTERMEASURE and THRESHOLD
- Thresholds = A procedure to classify assets.
- Countermeasure = Safeguard that somehow mitigates a potential risk
Security Principle:
Asset worth should be greater than what we spend on countermeasure
What is risk?
- Potential to unauthorized access to asset
- Potential to compromise of asset
- Potential to destruction/damage of asset
Asset Classification
Assets are classified to find out which asset has more cost in order to apply more security for it.
Following is classification of assets by different sectors
- Governmental Classification: (Unclassified, Sensitive but unclassified (SBU) , Confidential, Secret, Top Secret,
- Private Sector Classification: (Public, Sensitive, Private , Confidential)
Asset Classification Criteria
Following are factors on which classification criteria is based
- Value
- Age
- Replacement Cost
- Useful Lifetime
Roles based on asset classification:
- Owner (the group ultimately responsible for the data, usually senior management of a company)
- Custodian (the group responsible for implementing the policy as dictated by the owner)
- User (those who access the data and abide by the rules of acceptable use for the data)
Vulnerability Classification
Following is classification of vulnerabilities
- Policy flaws
- Design errors
- Protocol weaknesses
- Misconfiguration
- Software vulnerabilities
- Human factors
- Malicious software
- Hardware vulnerabilities
- Physical access to network resources
Common Vulnerabilities and Exposure (CVE)
The Common Vulnerabilities and Exposures (CVE) is a dictionary of publicly known security vulnerabilities and exposures.
National Vulnerability Database (NVD)
National Vulnerability Database (NVD) is a repository of standards-based vulnerability information;
Types of countermeasures
Administrative:
- These includes written policies, procedures, guideline and standards to protect assets on network
Physical:
- These include physical devices and infrastructure to implement security on network
Logical:
Logical countermeasure includes software and setting e.g. passwords, firewalls, intrusion prevention systems, access lists, VPN tunnels etc.
How to reduce Risk?
- Remove asset from network. E.g. do not place web server on internet. But then, how can public access web server?
- Transfer risk to someone else. E.g. Use a service provider to host your site. Now it is responsibility of service provider to provide security to your site
Potential Attackers
Following is list of potential attackers
- Terrorists
- Criminals
- Government agencies
- Nation-states
- Hackers
- Disgruntled employees
- Competitors
- Anyone with access to a computing device (sad, but true)
Attack Methods
Following is partial list of attack methods
- Reconnaissance
- Social engineering
- Privilege escalation
- Back doors
- Man-in-the-Middle Attacks
- Covert channel
- Trust exploitation
- Password attacks
- Botnet
- DoS and DDoS
Reconnaissance:
- Definition: This attack is used to discover who is present on the network
- Example: Launch one reconnaissance attack using nmap to find which IP address is present on network. Now again launch another reconnaissance attack to find which ports of particular host are open. Now try to exploit any of the known vulnerability that is associated with protocol on this port
Social engineering
- Definition: This attack is used to find user information by trapping user to perform an action of attacker’s will.
- Example: User click some link on spam email
- Types: Social engineering attacks can be further categorized as listed below
- Phishing attacks
- In phishing a link is presented to user that looks like valid trusted resource to user. On clicking this link, a page opens that ask user to enter sensitive information e.g. username/passwords.
- Pharming attacks
- User is redirected to a malicious url, where an attempt is made to disclose sensitive user information
- Phishing attacks
Privilege escalation
- Definition: In this attack first a less privilege access is achieved using some technique. Next using this less privilege access an attack is launched to get more privilege access.
- Example: Attacker gain user mode access to some host in intranet. From there attacker launches arp spoofing attack.
Back doors
- Definition: To access a compromised system in future, a backdoor application can be installed in it.
- Example: Normally backdoor are installed as a result of virus or worm
Man-in-the-Middle Attacks
Procedure:
- Attacker adjust himself between two communicating devices
- Attacker can see all the traffic
Man-in-the-Middle Attacks at Layer 2 (technique 1)
Procedure:
- ARP POISONING: Attacker spoof layer 2 address. i.e. every device thinks that mac address in frame is mac address of default gateway, but in reality this mac address belongs to attacker. This procedure is called arp poisoning
- Every frame now comes to attacker instead of going towards default gateway
- Attacker forwards the data to correct device.
- As a result of this procedure attacker has data from the communication.
How to mitigate Man-in-the-Middle Attacks at Layer 2 (technique 1)
Use techniques such as Dynamic Address Resolution Protocol (ARP) Inspection (DAI) on switches to prevent spoofing of the Layer 2 addresses.
Man-in-the-Middle Attacks at Layer 2 (technique 2)
Procedure:
- Attacker places a switch into the network.
- Using Spanning Tree Protocol (STP) manipulation attacker become the root switch.
- As a root switch attacker has the ability to see any traffic that needs to be sent through the root switch).
How to mitigate Man-in-the-Middle Attacks at Layer 2 (technique 2)
Use techniques such as root guard and other spanning-tree controls to mitigate this attack.
Man-in-the-Middle Attacks at Layer 3 (technique 1)
Procedure:
- Attacker places a rogue router on the network
- Attacker tricks the other routers to believe that the new router has a better path.
- This could cause network traffic to flow through the rogue router and allow the attacker to steal network data.
How to mitigate Man-in-the-Middle Attacks at Layer 3 (technique 1)
Use routing authentication protocols and filtering information from being advertised or learned on specific interfaces.
Best Practices to mitigate Man-in-the-Middle Attacks
- Use encryption for the confidentiality of the data in transit.
- If you use plaintext protocols for management, such as Telnet or HTTP, an attacker who has implemented a man-in-the-middle attack can see the contents of your cleartext data packets, and as a result will see everything that goes across the attacker’s device, including usernames and passwords that are used.
- Using management protocols that have encryption built in, such as SSH and HTTPS, is considered best practice
- Using VPN protection for clear text sensitive data is also considered a best practice.
Covert channel
- Definition: Use this technique to hide restricted data in allowed data
- Examples:
- Use of proxy sites to view content restricted in some area
- Backdoor application can send sensitive data using ICMP protocol
What is an overt channel?
Legitimate use of protocol is called overt channel. For example use of web browser to access web servers that server public content is over overt channel
Trust exploitation
- Definition: In this attack attacker first gain access to some less privilege region of network. This less privilege region is of more trust to inside network as compared to regions outside network. From this less privilege region, attacker can launch attack on inside network.
- Example:
- Data from outside network can enter Dematerialized Zone (DMZ).
- Data from outside network cannot enter inside network.
- Data from DMZ can enter inside network.
- Attacker first gain access to DMZ
- While on DMZ attacker can easily transfer any data to inside network
Password attacks
Definition: This attack is used to break password by trying all possible combinations for possible password. This is called brute force attack.
Best Practices to avoid Password Attacks: Specify limits on how many unsuccessful authentication attempts can occur within a specified time period
Botnet
Definition: In this attack a collection of already infected systems are used to launch much different type of attacks.
Example: Use of many infected systems to send TCP Syn repeatedly to same destination. This is called syn flooding. It will result in using victim host resources unnecessarily.
DoS and DDoS
Definition: In this attack so many packets are send to victim system that it becomes unresponsive
Difference between DoS and DDos
- In DoS attack a single machine is used to launch attack.
- In DDoS attack multiple distributed machines are used to launch attack.
Basic Principles and Guidelines while designing a network:
Rule of least privilege:
- Definition: Provide minimal access to required network resource
- Example: Open only required ports for protocols on your server. E.g. if you need to provide http(s) access, open port 80 and 443 and close all ports that are not needed.
Defense in Depth:
- Definition: This principle is best practice for implementing security. It states to implement security on every physical/logical device
- Example: First inspect packet contents (at router) as it enters your internal network through router. Next inspect packet contents using intrusion prevention system gateway before sending packet to any of the host. Finally inspect packet contents as it reaches to destination host.
Auditing:
- Definition: Auditing is a term used for accounting and bookkeeping of activities on network.
Separation of Duties:
- Definition: Divide security implementation into smaller tasks and assign these tasks to members with different roles.
- Application: By assigning new roles to members periodically, security policies in place can be reviewed by more than one member
- Example: Activities can be logged to accounting server. Using separation of duties approach, those members who perform activities should not have direct access to modify or delete logs on accounting server