Access Lists
Access Lists
In this article, you will learn about access lists commonly known as ACLs (Access Control Lists). We will cover IP based access lists, we have other types like MAC based ACLs, dynamic or reflexive ACLs but they are beyond the scope of this tutorial.
Access lists are used for 2 main functions:
- Filtering
- Classification
- Filtering: This is the technique used to allow or deny traffic. In ACLs, we use the keyword “permit” for allow and “deny” for disallow. We permit or deny some or all traffic to reach certain part of the network.
- Classification: This does not drops packets as filtering does, but it does classify the traffic and allows specific type of traffic. Most commonly used in terms of VPN where we would want to encrypt certain traffic or some QoS configurations (Quality of Service).

For example, see above picture, we want to encrypt traffic flowing from 192.168.1.0 /24 network but not the 172.16.1.0 /24 network. This can be using access-list to select traffic and is known as Classification.
In Access-lists configuration, we use certain statements, which are read / processed or executed in a top-to-bottom approach. For example:
An access-list looks like something below.
As per the top-down approach, and our example:
First the packet will try matching statement 10.
If statement 10 doesn’t match, then try to match statement 20
If statement 20 doesn’t match, then try to match statement 30
And if doesn’t match statement 30, then the packet is DROPPED.
If a match occurs then that statement is executed. Packets are usually permitted (forwarded) or denied (discarded).
NOTE: If we get a successful match, then the next statements are not read i.e. if the packet matched the statement 10 criteria then statement 20 and 30 would not be checked.
There is one more statement in the access list which is not visible, it is deny any statement. That come at the bottom of every access-list and means if we did not explicitly permit something or use a permit statement, it will be dropped. If nothing matches it comes to the last line which is “deny any”. This line is present but cannot be seen. J.
We have 2 main types of ACLs:
- ard ACLs ( 1 to 99 OR 1300 to 1999)
- Extended ACLs ( 100 to 199 OR 2000 to 2699)
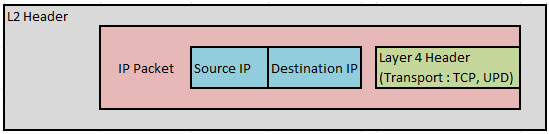
Standard Access-lists: It can only check for the “Source IP addresses”.
Extended access-lists: This type of access-list gives some more options. We can check source IP, Destination IP address and match on Layer 4, TCP or UDP port numbers.
Steps to create an access-list:
- Create an access-list globally and then assign it to an interface
- Can have only one ACL per interface, protocol and direction ( inbound or outbound)
- Have more specific statements at top of the access-list because once statement matches the below statement are not processed ( Top-down approach)
- The ACL number determines whether is a standard (1 -99) or extended (100-199) access-list
- Standard ACLs inspect only Source IP of a packet
- Extended ACLs inspect both source and destination IP and can also match Layer 4 protocols ( TCP, UDP, EIGRP, OSPF etc) and Layer 4 port numbers
- Standard ACLs should be place closed to destination and extended ACLs should be placed close to the source of transmission.
- Not to forget the “Deny any’ or IMPLICIT DENY statement at end of all the statements, Not seen but exists, so we must have a permit statement above.
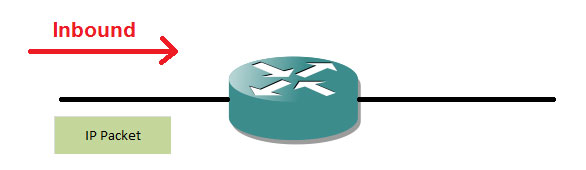
One more important concept, we should be known is the Direction where the access-list can be placed (Inbound and outbound)
Putting access-list as inbound on an interface means that all the packets that reaches the routes hits the access-list and will be checked against the statements in the access-list
In Outbound, the packets would go through the router and when they are leaving the interface, they will be checked against the access-list.
Wildcard masks
A Wildcard mask looks similar to a subnet mask. It is used to determine two things:
- Which part of the IP address mentioned should match EXACTLY
- Which part of the IP address can match ANY number
The wildcard mask looks like reverse of subnet mask. Let’s take an example:
Address: 192.168.1.0
Wildcard Mask: 0.0.0.255
As per the above wildcard mask, it would match any address which began with “192.168.1.” and the last octet could be any number.
While working with Access-lists and wildcard masks some rules to remember:
- If we have a bit set to 0 (zero) in a wildcard mask, the corresponding bit the IP address should MATCH EXACTLY. \
- If we have a bit set to 0 (zero) in a wildcard mask, the corresponding bit the IP address can match any number. It is also sometimes referred as “don’t care” bit.
Configuring ACLs consists of two steps:
- Configuring ACL statements in the global configuration mode
- Applying the ACLs on the interface to inbound or outbound traffic
STANDARD ACCESS LISTS
These only provide the functionality of filter based on one criterion i.e. source IP address. Based on this the router would determine if the packet should be forwarded or dropped. It means no further checks will be done like if the IP carries TCP, UDP or OSPF etc.
Depending on the source IP, the whole packet will be dropped or forwarded. It should be placed close to the destination network.
Syntax for creating access-list:
router (config) # access-list access-list-number {permit|deny} {host|source source-wildcard|any}
Syntax for applying access-list:
router(config-if)#ip access-group {access-list-number | access-list-name} {in | out}
Let’s take a scenario and work on it with basic configurations.
We have configured the IP addresses and enabled routing, thus all the networks are reachable to each other.
First, Let ping from 192.168.3.1 to 192.168.1.1, we see we get successful ping response.
Now, let’s say we want to block the network 192.168.3.1 from accessing the 192.168.1.1 network, we would need to write the below access-list on Router A.
In the above, the number 10 with access-list is the access list number and since it is in range of 1-99, it is a standard access-list.
The wildcard mask of 0.0.0.255 this will match (deny) all hosts on the 192.168.3.x network.
The next line with the ‘any’ keyword will match (permit) any other address other than the one mentioned in deny statement.
Now after creating the access-list we need to apply it using the below:
You apply it on the interface, closest to the destination.
Now to verify the configuration or to view all IP access lists configured on the router issue the below command:
Router# show ip access-list
The numbers 10 and 20 are line numbers; it shows the order or sequence of statements entered
To see on what interface we have configured the access-list you can use the command:
Router# show ip interface
We have configured it on S1/0; you can see it as below:
Also if you check the running configuration, you can see the access-list configuration.
Router# show running-config
Now, we have applied the access-list. If we check again by pinging to the 192.168.1.1 IP address, we see failure in ping. We see that the ip cannot be reached.
Router_Y# ping 192.168.1.1 source 192.168.3.1
EXTENDED ACCESS LISTS
These access-lists provide additional control compared to standard access-lists. They block based upon source, destination IP address and TCP or UDP port number. The normal practice is that extended access-list should be placed closest to the source.
Syntax for extended access- list:
access-list access-list-number
[dynamic dynamic-name [timeout minutes]]
{deny|permit} protocol source source-wildcard
destination destination-wildcard [precedence precedence]
[tos tos] [log|log-input] [time-range time-range-name]
Let’s consider the example:
If we had a webserver on the 192.168.1.x network having an IP of 192.168.1.1. Now you intended to block the network 192.168.3.0 from accessing other resources on the 192.168.1.0 network EXCEPT the webserver (HTTP port). We would need to create the below access-list on Router Y (Closest to the Source, so on Router Y)
The first line allows the 192.168.3.x network access only to port 80 on the web server.
The second line blocks 192.168.3.x from accessing anything else on the 192.168.1.x network.
The third line allows 192.168.3.x access to anything else.
To apply this access list, we would configure the following on Router Y:
NOTE: For editing access-lists, you cannot remove individual lines from a numbered access list. So you would need to delete and recreate the access-list to make changes. Best practice is to use a text editor to manage your access-lists.
Read more
- What is IOS
- Router Memory
- Router Startup
- Understanding of Router Prompts
- Help Features of Router
- How to Configure Hostname, Clock and set banner on Cisco Router
- Configuring Fast Ethernet and Serial Interfaces on Cisco Router
- How to save router configurations
- How to set passwords on Cisco router
- How to Backup Cisco Router IOS
- Cisco Router Password Recovery
- Router IOS Commands and Basic Router Configuration