Session Hijacking in Ethical Hacking
Session Hijacking
The concept session hijacking involves a hacker to take over an existing session between a user and host machine. By taking over the valid session the attacker then violates or exploits the session.
The attacker steals the valid session id which is used to get into the system and then snoop data.
One the attacker get the valid session, he can take over access of any authenticated device or resource like an ftp server, webserver or a telnet session.
Once the hijacker /attacker make a successful hijack, then he could play the role of a genuine user or can even silently just monitor / watch what communication is happening.
As a session is created for some specific time and during this time the client is authenticated by the server thus during this time the Server and client trust each other for the session. The data transfer that takes place during the session are not authenticated every time till the session is active and it is this benefit that the attacker takes and keeps on stealing information.
The danger when a successful session hijack is done is activities like data theft, identity theft and data corruption can take place. The traffic can be sniffed and the transaction can be recorded.
TCP Session hijacking means taking over a TCP session between two devices.
Blink Hijacking is another method where the response on the system can be assumed.
Man-in-the-middle attack is one common method where sniffing is used to track what is being communicated between two systems.
Steps involved in session hijacking:
– Track the connection
– Desynchronize the connection
– Inject the attacker’s packet
The following can lead to a session being hijacked
– No timeout set for invalid session ids
– Insecure handling
– Indefinite session expiry time
– Transmission of data in clear text
– Session id being small in length
Techniques of Session Hijacking
Brute force a session ID: This is similar to Brute Force passwords, where the attacker will try to guess the session id. The attacker would have some idea of the session ids available. The attacker could be benefited or helped with the uses of some malware, sniffing, cross site scripting or HTTP refreshers.
Steal the session ID: Sniffing can be used to steal a session id and then compromise the communication or the target.
Calculate a session ID: Some really good attackers could also calculate the session id based on the session id he seeing and can then guess or calculate the next session id thus understanding the sequence.
Hijacking v/s Spoofing
In spoofing the attacker pretends or fakes being someone else like a genuine user or computer. In this the session is not taken over by the attacker.
In hijacking the session is taken over by the attacker. The attacker would wait for the session to be established between two resources and then that session is taken over.
Process
- Sniffing: Using this technique the attacker should be able to sniff the traffic between the source and destination whose session he intends to take over.
- Monitoring: Observe the communication for some time and try to predict the sequence numbers. Here the attacker will observe the traffic flow and try to find patterns in the communication to guess the sequence numbers.
- Session Desynchronization: At times the communication can only occur between two parties, thus the attacker after taking over the session break the between the genuine client and server. He can either continue his session with the server acting as a genuine client or can prevent the client and server from doing any communication by just breaking their sessions.
- Session ID Prediction: This involves only predicting the session id based on which the attack will be made later.
- Command injection: This being the final stage, the attacker injects commands in the session trying to achieve what he want either data theft or identity theft etc.
Category of session hijack
a) Active attack: An active attack is where the attacker will take over the session from the client and communicate with the server. Here the client is being manipulated and the server is being fooled by thinking the attacker is a genuine user / client.
b) Passive attack: In a passive attack the focus is on monitoring the traffic or communication taking place between the client and the server. Sniffing software is sued in this situation where the traffic monitored and captured while going across the wire.
Session Hijacking in OSI model
- Network Level Hijacking : Interception of packets during the transmission or communication between client and server in a TCP or UDP session
- Application Level Hijacking: This involves taking control over a user’s HTTP session by obtaining the session ids.
Session IDs can be seen in:
– In the embedded URL that is received by the GET request for the application
– In the hidden fields of a form
– Client machine’s would have it in the cookies
Application Level Session Hijacking
This involves taking control over a user’s HTTP session by obtaining the session ids. By obtaining the respective session ids and unique identifier of HTTP sessions, the HTTP session can be hijacked. The session token can be compromised by one of the follow:
– Predictable session token
– Man-in-the-middle attack
– Client side attacks ( XSS, Trojans etc)
– Man-in-the-browser attacks
– Session sniffing
Session sniffing: Using a sniffer the attacker captures a valid session token which is called the “Session ID”. The attacker then uses this valid token session to get unauthorized access to the webserver. If the traffic is unencrypted the session ids can be determined easily. This unencrypted session can also have username and passwords information.
The above figure shows the representation of how a valid session id between the Client and server is hijacked by the attacker and then used the same session id to communicate with the server by spoofing itself as a genuine client.
Predictable Session Token: This is a method of hijacking or impersonating a website user. When a client tries to access a website, the website will try to authenticate and track the user identity. Only once the authentication is done then the website will share the data.
When a user submits the username and password, the website will generate the unique “session id” and this session id shows that the user is authenticated to access the website. All subsequent communications will have this session id tagged as a proof of the authenticated session.
If this session id is with the attacker, he can access the website as the genuine user.
If the attacker captures the below session ids:
http://www.abc.com/view/ABCD20022015162820
http://www.abc.com/view/ABCD20022015180220
http://www.abc.com/view/ABCD20022015191810
We see some similarities in the session id, example in this session id: ABCD20022015162820
ABCD: this part is constant
20022015: is the Date (20-02-2015)
162820: is the Time (16:28:20)
Thus from learning the above pattern the attacker can predict the session id for a time:
13:05:00 on 25th Feb 2015
http://www.abc.com/view/ABCD25022015130500
Man-in-the-Middle-attack (MITM)
In this the attackers get in middle of an existing connection between two or more computers and intercept the messages. The entire communication goes though the attacker.
The victim’s messages go to the attacker and the attacker then sends it to the server. And in reply the server sends some message which again goes through the attacker sitting in middle. Both the client and server are unaware that they are not communicating directly and someone is sitting in middle and intercepting the messages and relaying them.
The complete MITM takes place in a two phase, like:
– Client to attacker
– Attacker to Server
Network Level Session Hijacking
This involves hijacking Session and transport protocols. These include:
– TCP/IP hijacking
– IP spoofing
– RST Hijacking
– Blind Hijacking
– Man-in-the-middle: packet sniffer
– UDP hijacking
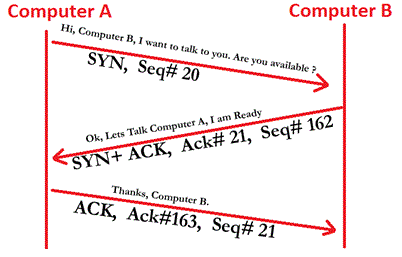
TCP communication between two parties takes place with the help of a 3 way handshake which involves:
– Client initiates a connection by sending an ISN – Initial Sequence Number and setting the SYN flag
– On receipt of this packet the server then acknowledges the packet and send its own SYN along with Acknowledgement ( ACK)
– On receiving this packet the client acknowledge the server sequence number by incrementing it and setting the ACK flag.
Session Hijacking Tools
– Zaproxy ( OWASP Zed Attack Proxy)
– Burp Suite
– JHikack
– PeterJack
Countermeasures against Session Hijacking
– Use string or long random number for Session id
– Use secure shell ( SSH) for communication
– Pass authentication token over HTTPs
– Implement logout option for user session to close
– Generate session id after successful login
– Have encrypted data be passed between users and webservers.