Trojans and Backdoors
Trojans and Backdoors
Hackers do make use of Trojans and backdoors to get access to a system. Both of these are installed on the target system but with the use of some other program or by somehow making the user on target system install your program.
Trojans and backdoors come under the category of malware which is used to compromise a target system. When the Trojan reaches a target system it looks like a genuine application or software that makes the user click and install it. But eventually it was sent in disguise to the target system.
Once these Trojans and backdoors are installed the system becomes slow and it does crash often as it eats up resources of your system. Also if connected to the internet it can cause data theft and transfer some info out of the target computer.
Once such malware is installed, a hacker can then use the target system to attack other systems. Mainly such techniques are used for DDoS (Distributed Denial of Service). If it’s a key logger then the Trojan can also make notes of all the keys types on the system. Such Trojans are also capable of taking screenshots of screen.
As trojans are sent along with some useful programs, below are ways how the Trojans are sent to the victim’s system.
– Using Instant messaging or chat: While having a chat discussion, someone may share a picture with your or a video asking you to have a look at the latest phone etc, but be careful in opening such images etc from unknown people.
– Email attachment: You may receive an email that looks genuine, like from your Bank or some friend’s name, asking you to click a link and update your contact details etc. by clicking such link you download the Trojan on your system and thus get compromised.
– Using File sharing: You may be in need of some application of video and there are attackers around who would mask the Trojan with the required file and share it using pen drive, or Internet, email etc.
– Any program that can be downloaded from Internet: Some good application or even video of your favorite celebrity or sportsperson can be shared provoking you to click the click or see the video and thus in turn get a Trojan or backdoor installed on your computer.
Making use of advertisements when browsing data are major sources of such malware. The advertisement shows that it allows downloading free software which the victim may be interested in but finally he is downloading a Trojan.
Some common Trojans are as below:
Deep Throat -> UDP -> Port 2140, 3150
Net Bus -> TCP -> 12345, 12346
Back Orifice -> UDP-> 31337 or 31338
Backdoor as it name suggest, is used for reentry into that target system by the attacker. This program is installed and the victim is not aware of it and the service for this backdoor is running on the victim’s computer with a name that sounds genuine so the victim does not know that his system is compromised.
RATs (Remote Access Trojans) are types of backdoor through which the attacker takes remote control of the system. These RAT applications are installed on the victim and attacker computer. The RAT server is installed on the victim and RAT client on victim’s computer, thus the attacker can connect to the server (victim). Once can make out if a RAT is installed on their system if the movement of mouse is observed on its own and some popup opening.
Overt and Covert Channels
If a program uses the normal or legitimate way for communicating with the system is known as Overt Channel.
Using Programs or communication path that is not normal and intended is considered COVERT Channel.
The Trojans installed on the victim’s computer use the covert channels. Attacker can also form tunnels where one protocols can be carried over another protocol.
Types of Trojans
– RATs (Remote Access Trojan) : Gain Remote control of victim
– Destructive Trojan: Corrupt or delete files
– DoS ( Denial of Service) Trojan: Launch a DoS attack
– FTP Trojan: Create FTP server and copy files onto it. E.g. TinyFTPD
– Data Sending Trojan: Send data from victim to hacker’s computer
– Proxy Trojan: Use victim’s computer as Proxy to attack another victim
– Command shell Trojan: Netcat is a command line tool that is popularly used command line tool through which TCP/ UDP ports can be opened on the target system. Then these open ports are used by the attacker with telnet to gain access and control the target.
Email Trojans: Access to victim’s computer is taken using sending email and having them click a link.
VNC Trojan: The victim’s computer is controlled by the attacker using VNC server. Since VNC is considered a utility, these are not detected by the antivirus as problematic. E.g. WinVNS, VNS stealer, etc.
Botnet Trojans: Botnet is a group of software robots that run automatically. These robots are nothing but worms, Trojan horses etc. E.g. NetBot Attacker, Illusion Bot.
Some GUI tools are also available like MoSucker, Jumper and Biodex.
How to attack Systems using Trojan
- Making use of a Trojan Horse Construction Kit, a new Trojan packet is created.
- A Dropper is created; this is part of the malicious code in the trojanized packet which is to be installed on the target.
- Making use of wrapper tools to create a wrapper and have it installed on the victim’s computer. Tools that be used are: Graffitti.exe, Elite Wrap etc.
- Transfer this Trojan to victim’s computer. It can be done via using normal means like pen drive, floppy etc and copy it to victim’s computer or they can be spread using emails, chats, network sharing etc.
- Execute or run the dropper, using this dropper the malware is disguised making the victim feel that the application or link is genuine. After the victim’s computer is infected with one malware, it then helps other malware and unwanted programs to be installed on it.
- Finally execute the damage routine, which means that do the action that the Trojan actually wanted to, like copy some files and send to attacker, delete important files or even format the hard disk of the victim.
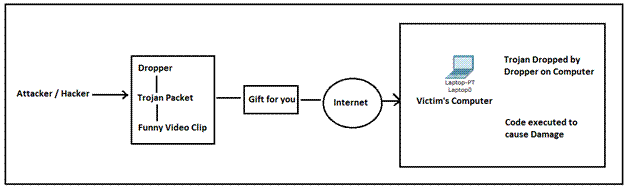
The above picture demonstrates the steps taken by an attacker. The Attacker, making user of a Dropper, take a Trojan and combines it with a Funny Video Clip and shares it you as a Gift. Once the victim open that video for viewing, the dropper will drop the Trojan on the system and then it may be executed to cause damage.
Wrappers: are tools that help a Trojan to be bound with a genuine looking application. When this wrapped exe or image is clicked, the main Trojan is installed on the victim’s computer in background while in foreground the wrapper application is being installed. Wrappers are also known as guleware, as it sticks other application or exe’s with itself.
Some wrapper programs are: Kriptomatik, SCB Lab’s Professional Malware Tool,
Evading Antivirus
Hackers use some techniques to avoid being caught by the anti-virus programs:
– Do not uses downloaded Trojans from web
– They write own Trojans
– Rename Trojan files to different application names like :
- Exe to vbscript
- Exe to .xls file
- Exe to ppt
- Exe to mp4
– The checksum value is changed so signature does not match and IDS cannot detect it
– Send multiple parts than once on the target system are combined to make one Trojan file.
How to detect Trojan
- Look for unnecessary open ports using tools like TCPView, CurrPorts
- Look for unnecessary services using tools like, Process Monitor, What’s running
- Scan for registry and remove unwanted entries using tools like Registry Cleaner, Registry Mechanic
- Scan the system for device drivers that are not used using tools like Driver View, Driver Easy
- Check startup programs using tools like starter, Security Auto run, Active Startup
- Remove suspicious files and folder on the system using tools like FCIV- File checksum Integrity Verifier, Tripwire, Sigverify
- Run scanners to detect trojans using tools like Trojan hunter etc.
Trojan Countermeasures
– Avoid downloading unknown application from the Internet and untrusted sources
– Keep the system patches with latest security updates
– Scan external media like floppies, CDs, pen drives etc before copy content from them
– Run firewalls and antivirus software on your system with latest definitions
– Keep protection on your system to avoid unauthenticated access and installation of applications
Backdoor Countermeasures
– Understand the danger of being compromised, always be cautious while accessing Internet and opening emails
– Use Antivirus with latest definitions and patches
– Keep applications updated with latest security patches.
Some tools like Trojan Hunter, Emsisoft Anti-Malware, and Trojan Remover can also be used to remove Trojans from infected computers.
Read more
- What is Ethical Hacking
- Footprinting and Reconnaissance
- Scanning Networks
- Enumeration Hacking Phase
- Sniffers
- Social Engineering
Read more