Footprinting and Reconnaissance
Footprinting and Reconnaissance Tutorial
Footprinting is process of collecting as much information as possible about a target system /network for identifying different ways of intruding an organization’s network.
Process involved:
- Collect basic info
- Find OS version, Webserver edition etc.
- Get DNS info using Whois etc
- Look for vulnerabilities and exploits for launching attacks.
It is the first step in ethical hacking which involves collecting info about target and its environment. Important information can be collected in this stage which is then helpful in further stages of Ethical hacking.
Passive Information Gathering: Using this means, the hacker will get information about target from publically accessible sources and this is also called Open source Footprinting. In this type of information gathering no direct contact with the target organization is required e.g. TV, newspaper, social networking. Details can also be collected like IP address boundaries, OS details, Webserver software, TCP, UDP services on the system.
Active Information Gathering: This type of information gathering involves getting data through social engineering, on-site visits, and interview questions. Try to collect info from some insider or employee of the Target Company or organization.
Anonymous Footprinting: Gather from where author of information cannot be identified. Collect info anonymously so efforts cannot be tracked back to you.
Pseudonomous Footprinting: Collect info that might be published in a different name to keep privacy. Published on Internet but not directly linked to author’s name. Author may use pen-name.
Private Footprinting: From organizations websites, emails, calendars etc
Internet Footprinting: Collect info from Internet
Why Footprinting
It is very important understand current security position of the organization. Based on the currently security position, you can look for loopholes and make plan accordingly.
So the attack can be specific based on area of weakness, IP, DNS etc
Attacker can build his own DB and use accordingly for attack. It can be helpful to understand the network diagram of the target. Tracert is used popularly.
Objective of Footprinting
Collect Network info: Domain Name, running services, VPN Points, ACLs etc using Whois Database analysis and tracert
Collect System Info: User and Group names, Passwords, Routing tables, SNMP
Collect Organization info: Employee names, address and phone number, HTML source code, CEO name, job skills etc.
Footprinting Threats
– Social Engineering: Gathering information using non-technical means.
– System and Network Attack
– Information Leakage
– Privacy Loss: Once u access system and escalate privileges, their privacy is lost. Can access tender etc.
– Corporate Espionage: competitors can spy an attempt to steal sensitive data. Competitors can launch similar products in market causing loss to the initial company.
Footprinting Methodology
Through search engines: In today’s world almost everyone would have registered on some website and you may have put your email / phone on some registration website. Google, Yahoo, Bing are search engines and can be helpful to search employee details, intranet page.
Reconnaissance is also a term that means collecting information about the target before attacking it.
There are 7 stages of Reconnaissance
1. Gathering Info
2. Locate the network range
3. Active machine s to be identified
4. Find open ports and applications
5. Detect Operating System
6. Fingerprinting services
7. Map the network
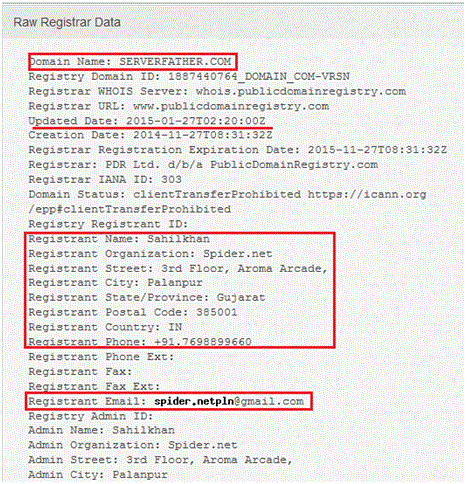
Whois is an important tool that can be used to collect information about a target. This would give information about the domain registrant, domain servers, contact details etc. It collects DNS related information from a URL.
In Linux this utility is inbuilt but for Windows you need to use some 3rd party tool or some online websites like:
www.samspade.org
www.allwhois.com
www.dnsstuff.com
https://who.is/
See below example from https://who.is/
Enter the domain name, i.e. URL or IP address of the webserver.
In this case I will use: serverfather.com
Nslookup is a program to query Internet Domain servers.
Footprinting through Search Engine
The hacker can make use of Search Engine to get information about the organization, its employees, headquarters etc.
One can go to the wikipage and get some information. They can also browse images of their offices to understand the physical location and infrastructure and then use this information in their next phases of attack.
We can find URLs for an organization using search engines. Deeper checks may also get you URL of their ftp servers or intranet URLs.
Location footprinting
Using features of Google maps, you can get more detailed view of organizations and directions to reach to their offices. How the surroundings look, which other nearby cafes etc are nearby from where the hacker can watch the office reception or premises.
People Search or Footprinting
A hacker can also search for employee names working in an organization using LinkedIn, Facebook etc. Also can search on Internet for the employee name and you will get good information about him.
People search also can take place using Social networking sites like twitter, Facebook, LinkedIn and also job sites.
As we access financial sites these days, even our banking information can be collected by hackers if they are closing watching the traffic flowing through our network. Thus most financial institutions use encryption and SSL for such transaction.
Also valuable information can be extracted from the website page, using the View Source option.
Website footprinting
Using some tools, a hacker can create a clone of your website which is a mirror of your site, they can then use this to send the link to end users and gather their information. One such tool is HTTrack Website Copier (https://www.httrack.com/)
Email Footprinting
Tools that are used for email tracking can reveal information of email headers, IP address, location from where the email came etc.
A popular tool used is: Email tracker pro (http://www.emailtrackerpro.com/)
Footprinting using Google
Google offers some operators through which you can search specific information. We have may such Google operators like:
1. Define: Will give the definition of the work you mention.
2. Allintitle: This will show results that has the text mentioned after the “allintitle” operator
3. Filetype: Give search results of the file type you mention. E.g. Filetype: pdf, will result link that have pdf files.
4. Inurl: will give results for the text you mention with the operator. E.g. Inurl: Microsoft will give results of links that have ‘microsoft’ in the URL.
DNS footprinting
A tool like DNS stuff can be helpful in getting DNS related information from a URL or domain name. http://www.dnsstuff.com/
Footprinting using Traceroute
Traceroute or tracert is the command that is used to check connectivity to a destination and the path that it follows. It uses ICMP packets which are routed to a destination nearby and then till the end or destination. With this you can get the IP address or hostname of each point in the path.
https://www.pathanalyzer.com/
Path Pro Analyzer is a GUI tool that is similar to traceroute.
Read more
- What is Ethical Hacking?
- Scanning Networks
- Trojans and Backdoors
- Enumeration Hacking Phase
- Sniffers
- Social Engineering
Read more