VLAN
VLAN – VIRTUAL LAN
As all of you may be aware of the word LAN (Local Area Network), it is a network of computers operating in a local area like a lab or small office or school etc.
A VLAN is a Virtual LAN, which means it creates a LAN virtually which cannot be seen physically but based on the operations and functioning, you feel as if we have multiple LANs.
Let us understand some other concepts to understand VLAN better.
- Collision Domain
- Broadcast Domain
A hub in a network operates as half-duplex that means it can either send or receive traffic at a time. In such a case if we have two devices that try to communicate simultaneously we have a collision. (Only one device can communicate at a time). The ports on a hub belong to same collision domain i.e. a physical segment where collision can occur is called the collision domain.
The above picture shows, 4 computers connected to a HUB. If any two or more computers send traffic at the same time, we have collisions. Also note that a broadcast sent by one computer is received by all other devices connected to the hub.
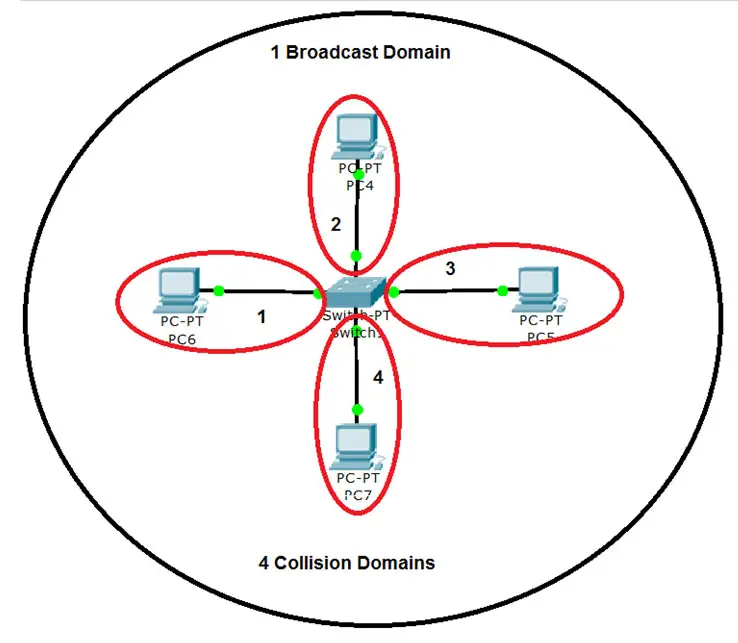
Switches operate as Full duplex, thus each port can send and receive simultaneously and has its own collision domain. Since each port is a separate collision domain chances of collision are very less.
The above picture shows that 4 computers connected to a Switch, have 4 collision domains, one for each port. Thus simultaneous communication (full-duplex) is possible without collisions. So with the use of switches we break the collision domain, in effect reducing collisions.
Both Hubs and Switches belong to one broadcast domain, which means that a broadcast or multicast is forwarded out each port of the device. A logical segment of network in which a broadcast or multicast propagates is called the broadcast domain.
See the above picture; we see 4 collision domains and 1 Broadcast domain. It means that if any of the devices connected to the switch send a broadcast, it would reach all devices connected to the switch.
Consider a corporate with thousands of computers and other devices, in such case if one device sends a broadcast message, it is received by all and causing unwanted traffic on the network.
A corporate may have several departments like Finance, HR, Sales, Marketing, IT etc. and everyone connected on the network. If a Sales person sends a broadcast for his other colleagues it reaches to all the other departments also causing unwanted traffic. To overcome this issue VLANs come to our rescue.
PURPOSE of VLAN:
VLAN will divide a single physical network into several logical networks. When we divide the network in separate VLANs, the devices in one VLAN cannot communicate with the VLAN in another. They need a router to communicate because once you create a VLAN you are creating a new network. And for different networks to communicate with each other we need a Layer 3 device like Router.
Based on different requirements we design devices to be in separate groups. We can assign each group to a separate VLAN so they can interact among each other, but cannot interact with the other group or department.
E.g. we may have many Human Resource staff and would like them to be in one group as they may be accessing certain applications.
The Finance Team may be using some other applications and would not want others to be able to interact with their applications.
So we put these departments in different VLANs which isolate them from each other, thus also providing security.
If you see the above figure we have 2 broadcast domains, because we have put Finance and HR in different VLANS. If a PC from Finance sends a broadcast, it will only be received by the other PC in Finance VLAN and not by anyone in the HR VLAN; this avoids unnecessary traffic on the HR PCs.
Features of VLAN:
- Each VLAN is considered an independent LAN
- Reduces congestion on a large LAN
- Provides security as other VLANs cannot access it ( Layer 2 Security)
- Can group computers / users with similar functionalities/roles in one VLAN
- VLANs can be named for ease of understanding
- Using VLANs we can divide one physical switch to act as multiple logical switches
- Divides single broadcast domain to multiple broadcast domain ( Each VLAN has will have its own broadcast domain)
- Cisco Devices have VLANs enabled by default.
- All ports of the switch are in VLAN 1 by default. VLAN 1 is called the Management VLAN
Configurable VLANs range from 2 – 1001
Now let’s see further about configuring a VLAN. We need to assign individual switch ports to a VLAN. A VLAN can have one or multiple ports. Only devices in same VLAN can communicate with each other.
As per the above picture:
If you see we have logically divided one Physical Switch (Switch A) to two logical switches. (Blue and Green VLANs operate as separate switches)
Since devices in same VLAN can communicate, A-1 and A-2 and communicate with each other and A-7 and A-8 can communicate with one another.
Devices in Blue VLAN cannot communicate with VLAN Green, because now there are two separate networks and need a Router to communicate.
As we configure these VLANs manually on ports and hence called Port-based (untagged) VLANs. We have to assign each port on a switch to a VLAN.
NOTE: Multiple ports can be a part of a VLAN, but a port cannot be part of multiple VLANs.
Ways to create VLANs:
- Using Config Mode
- Using VLAN Database (Older method, will not be used in newer Cisco Switch models : Not covered in this article)
The below commands are used to create a VLAN in Config mode. Create VLAN with VLAN number and assign a name to it.
Switch(config)#vlan <vlan number>
Switch(config-vlan)# name <vlan name>
Switch(config-vlan)#exit
The below command will assign ports to VLAN using Config Mode:
Switch(config)# interface <interface type> < interface number>
Switch(config-if)# switchport mode access
Switch(config-if)# switchport access vlan <vlan number>
We need to specify the interface type, like FastEthernet or Ethernet etc and then the interface number like 0/1 or 0/2 etc.
The command ‘switchport mode access’ tells the switch that this is an access port and is connected to a computer and not another switch.
For VLANs on two or more switches to communicate with each other, we need to use TRUNK ports.
The command ‘switchport access vlan <vlan number>’ put the interface in the specified vlan.
To Verify VLAN configuration, we use the below command on a Switch:
Switch# show vlan
TIP: We can use the range command on the switch to configure multiple ports simultaneously.
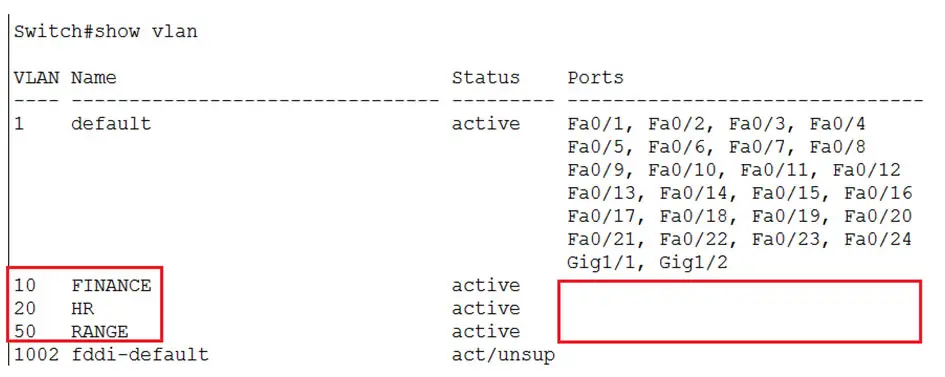
We see the use of it below where we create a new VLAN (VLAN 50) and add multiple ports to the VLAN.
The below command adds ports fa0/5 through fa0/7, fa0/10 and fa0/14 to VLAN 50.
We can verify it using the ‘show vlan’ command.
Now let us try some configurations, in the lab. We have switch connected to 4 computers and all the computers are in the network 192.168.1.0/24
On the switch, see the default configuration.
We see VLAN 1 as default and all the ports are assigned to VLAN 1. We also see other default VLANs (e.g. 1002 fddi-default) which are not used currently are unsupported (act/unsup)
We login to one of the computers and try to ping the othe
When we ping each computer we get a response and all are reachable since they are all in the same network and same VLAN i.e. VLAN 1
Now let’s dive into VLANs creation.
Create VLAN 10 and VLAN 20 and name them, FINANCE and HR respectively.
 Add interfaces fa0/1 and fa0/2 to VLAN 10
Add interfaces fa0/1 and fa0/2 to VLAN 10 Add interfaces fa0/3 and fa0/4 to VLAN 20
Add interfaces fa0/3 and fa0/4 to VLAN 20 By creating 2 VLANs and adding interface in separate VLANs we have created two logical networks.
By creating 2 VLANs and adding interface in separate VLANs we have created two logical networks.
Devices connected to interface fa0/1 and fa0/2 can communicate since there are in same VLAN and the interfaces fa0/3 and fa0/4 can communicate with each other, but these 2 VLANs cannot communicate with one another.
On the switch verify the VLAN configuration that we did, it shows two VLANs created and respective ports assigned to them.
 Now let’s test if both VLANs can communicate with each other.
Now let’s test if both VLANs can communicate with each other.
We see that IP: 192.168.1.2 is reachable because it is connected to interface fa0/2 which is in the same VLAN as interface fa0/1 (192.168.1.1)
But we get failure while pinging to 192.168.1.3, since it is connected to interface fa0/3 and is part of VLAN 3.
All the VLANs are stored in a database file called the VLAN.dat.
If VLANs need to be deleted only doing the ‘write erase’ will not help, the VLANS that we create still exist in the VLAN.dat file.
You can see the file in flash:
If we just do a write erase and reload the switch. We observe that the configuration has been deleted from the ‘show running config’ but when we check ‘show vlan’ we still see the VLANs that we created. The interface assigned to them have been deleted and gone back to default VLAN i.e. VLAN 1.
So to delete the VLANs permanently we need to delete the VLAN.dat file.
 When we are prompted for confirmation, press Enter
When we are prompted for confirmation, press Enter
Now reload the switch.
 And verify the VLANs again, using ‘show vlan’
And verify the VLANs again, using ‘show vlan’
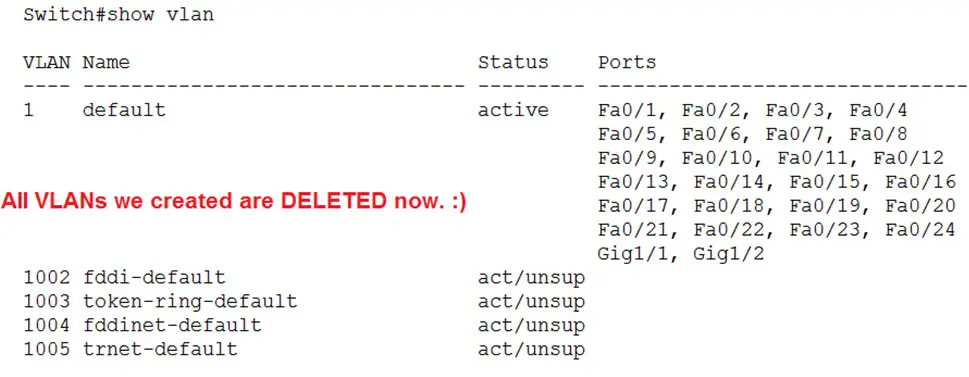 All VLANs are deleted and the switch is back to normal without VLANs
All VLANs are deleted and the switch is back to normal without VLANs